You may or may not be able to install Windows 7 on your particular Windows 8 PC. A lot of that depends on the hardware. And, of course, you’ll have to buy a new copy of Windows 7.
But if you or a close family member hates Windows 8 that much (and I’m in complete sympathy), there are better options than paying for two versions of Windows and only using one of them.
First, see if you can return the computer. The retailer or manufacturer may have a 15- or 30-day return policy. If you bought the PC recently enough, you can probably get your money back--minus a restocking fee.
And then, you can buy a Windows 7 PC. Yes, they’re still available, although your choice of models will be considerably smaller. The major manufacturers all have search tools on their websites, where you can select criteria for your preferred computer. Check the operating system option to see if it includes Windows 7.
While writing this article, I found three Lenovo laptops, four HP laptops, and a whole lot of Dell laptops and desktops available with Windows 7. Senior editor Brad Chacos has further advice on how to get a Windows 7 PC.
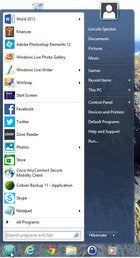
If your PC can’t be returned for a reasonable price, you can make Windows 8 behave very much like Windows 7. With far less work than it takes to reinstall an alternate operating system, you can create a reasonable facsimile of Microsoft’s best user interface.
First, you need a third-party Start Menu program. There are many out there, but my favorite is the free Classic Shell. It creates a very close approximation of the Windows 7 Start Menu, with all of the features in the right places.
When you set up Classic Shell, go to the Start Menu Settings tab and select Windows 7 style. Near the bottom of the Basic Settings tab, be sure to check Skip Metro screen. You’ll never have to see that dumb home screen again.
Classic Shell includes more than just a Start Menu replacement. It can also return Internet Explorer and File Explorer (the Windows 8 equivalent to Windows Explorer) to their old selves.
What Classic Shell can’t do is turn off the charms that appear when you mouse too closely to the corners of your screen. Fortunately, there are other ways to do this.
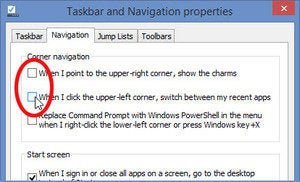 One such solution is built into Windows 8.1. Unfortunately, this solution doesn't disable the bottom-right corner.
One such solution is built into Windows 8.1. Unfortunately, this solution doesn't disable the bottom-right corner.If that’s alright by you, right-click the taskbar and select Properties. Click the Navigation tab.
Uncheck both When I point to the upper-right corner, show the charms and When I click the upper-left corner, switch between my recent apps.
 To disable all of these corners, forget the instructions above and use the Winaero Charms Bar Killer. When you launch this free program, it goes directly to the notification area. Right-click the icon for options.
To disable all of these corners, forget the instructions above and use the Winaero Charms Bar Killer. When you launch this free program, it goes directly to the notification area. Right-click the icon for options.Source - PC World